How to Configure IPSec Host to Host Tunnel with RSA Keys
Version 0.1 (02 May 2018)
Overview
Host to Host configurations allow two nodes to establish a tunnel between them. The encrypted communication will be limited just to the two nodes involved.
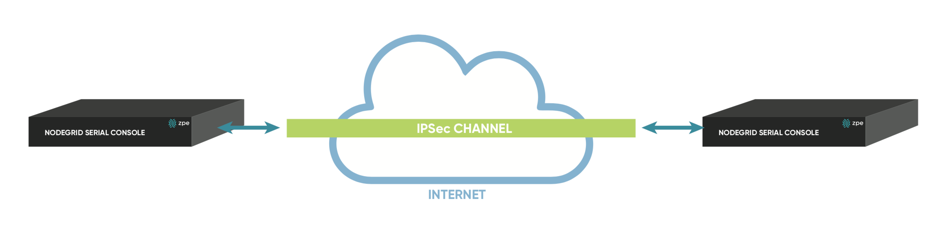
Figure 11: Host to Host Configuration Example Details
Host to Host with RSA Key
Required tasks:
- Prepare both nodes (see: How to Prepare a Nodegrid Node for IPSec)
- On both nodes create an RSA Key (see: How to create RSA Keys for IPSec)
- Create connection configuration file in /etc/ipsec/ipsec.d/ directory as root user
- Copy the configuration file only to the other node. The Secret File dose not need to be copied in this case
- Restart IPSec service on both nodes
- Confirm that the tunnel was established
- Short information
- More Detailed Information
| Fields | Values | Comments |
|---|---|---|
| Connection name | <String> | |
| leftid | @West | Identifier for the west/left site. Values can be: %left - uses left as value @<STRING> - uses the string The leftid values is used to identify the PSK |
| left | <IP or FQDN> of the West/Left host | Additional to an actual IP address can the following values be used. These are resolved when the service starts. %defaultgateway %eth0 |
| leftrsasigkey | Public RSA Key | |
| rightid | @East | Identifier for the East/right site. Values can be: %right - uses left as value @<STRING> - uses the string
The rightid values is used to identify the PSK |
| right | <IP or FQDN> of the East/Right host | Additional to an actual IP address can the following values be used. These are resolved when the service starts. %defaultgateway %eth0 |
| rightrsasigkey | Public RSA Key | |
| authby | rsasig | |
| auto | start | The setting regulates when the IPSec tunnel will be established. Following values are accepted: add (manual start), start (starts with the service), ondemand (will be established if traffic exists), ignore (connection will be ignored and not used) |
| connaddrfamily | ipv4 | Possiable values are ipv4 or ipv6 |
Format:
conn
connaddrfamily=ipv4
auto=
authby=secret
leftid=
left=FQDN>
leftrsasigkey=
rightid=
right=FQDN>
rightrsasigkey=
Example /etc/ipsec/ipsec.d/host-to-host-rsa.conf
conn host-to-host-rsa
connaddrfamily=ipv4
auto=start
authby=rsasig
leftid=@West
left=192.168.50.4
leftrsasigkey=0sAQO1Gr2MY41qhG…………….bbtc7lkT+TxtPBE7sSBWkHr1C5aalkYLwL9kfgK0i7w==
rightid=@East
right=192.168.58.4
rightrsasigkey=0Vaixy810IkQzUU+SmxA6O………..WORl0i3K43tZx9aakmMyvanRg7Bwz4R+ssDe4+MwsGP0=
root@ng-west:~# ipsec restart Redirecting to: /etc/init.d/ipsec stop Shutting down pluto IKE daemon 002 shutting down Redirecting to: /etc/init.d/ipsec start Starting pluto IKE daemon for IPsec: . root@ng-west:~#
root@ng-west:/etc/ipsec/ipsec.d# ipsec whack --trafficstatus 006 #4: "host-to-host-rsa", type=ESP, add_time=1524097790, inBytes=0, outBytes=0, id='@East'
root@ng-west:~# ipsec whack --status |grep host-to-host-rsa ……………. 000 #4: "host-to-host-rsa":500 STATE_QUICK_R2 (IPsec SA established); EVENT_SA_REPLACE in 28035s; isakmp#3; idle; import:not set 000 #4: "host-to-host-rsa" esp.51e306d2@192.168.58.4 esp.7bdcb6d9@192.168.50.4 tun.0@192.168.58.4 tun.0@192.168.50.4 ref=0 refhim=0 Traffic: ESPin=0B ESPout=0B! ESPmax=4194303B 000 #3: "host-to-host-rsa":500 STATE_MAIN_R3 (sent MR3, ISAKMP SA established); EVENT_SA_REPLACE in 2835s; lastdpd=-1s(seq in:0 out:0); idle; import:not set 000 #5: "host-to-host-rsa":500 STATE_QUICK_I2 (sent QI2, IPsec SA established); EVENT_SA_REPLACE in 27555s; newest IPSEC; eroute owner; isakmp#2; idle; import:admin initiate 000 #5: "host-to-host-rsa" esp.acd469a4@192.168.58.4 esp.6b948bad@192.168.50.4 tun.0@192.168.58.4 tun.0@192.168.50.4 ref=0 refhim=0 Traffic: ESPin=0B ESPout=0B! ESPmax=4194303B 000 #2: "host-to-host-rsa":500 STATE_MAIN_I4 (ISAKMP SA established); EVENT_SA_REPLACE in 2114s; newest ISAKMP; lastdpd=-1s(seq in:0 out:0); idle; import:admin initiate
Related Articles
How to Configure IPSec Host to Site tunnel with RSA Keys
Version 0.1 (02 May 2018) Overview Host to Site configurations are very similar to Host to Host configurations, especially the authentication methods are the same. Added changes to the configurations are the values for rightsourceip and ...How to Configure IPSec Site to Site Tunnel with RSA Keys
Version 0.1 (02 May 2018) Overview Site to Site Configurations are further extension to host to site configurations. Communication is in this case expanded between multiple subnet on both sites of the connection. Subnet and communication IP addresses ...How to Prepare a Nodegrid Node for IPSec
Version 0.1 (02 May 2018) Overview Nodegrid comes with all the required tools to run and configure IPSec pre-installed, but IPSec is by default not configured and a few preparation steps on every node need to be performed before the first VPN ...How to create RSA Keys for IPSec
Version 0.1 (02 May 2018) Prepare RSA keys In case Raw RSA keys will be used for the IPSec authentication then these keys need to be created before they can be used in the configuration later. Each RSA Key has a private key which needs to be stored ...How to Configure IPSec Host to Host tunnel with Certificate
Version 0.1 (02 May 2018) Overview Host to Host configurations allow two nodes to established a tunnel between them. The encrypted communication will be limited just to the two nodes involved. Figure 11: Host to Host Configuration Example Details ...