How to Prepare a Nodegrid Node for IPSec
Overview
Nodegrid comes with all the required tools to run and configure IPSec pre-installed, but IPSec is by default not configured and a few preparation steps on every node need to be performed before the first VPN connection can be tested. This section outlines the individual steps required.
The configuration can currently only be performed through command line tools or automation methods which utilizes the shell. The configuration has to be performed as the root user.
This file contains the configuration settings for the services and configuration options which might apply to all configurations.
Prepare Nodegrid
The IPSec services is fully installed but not yet configured on the Nodegrid solution. To enable the service, perform the following steps. All of these steps only need to perform once on each node.
All steps below assume that they are executed as the root user.
- Configure a valid and unique hostname and domain name. Depending on the Authentication method can these not be changed later.
- WebUI
- Login to the WebUI with an admin user
- Navigate to Network::Settings
- Populate the values for Hostname and Domain Name with appropriate values
- Initiate the NSS DB
- Initialize DB
- Configure Firewall
- UDP port 500 for the Internet Key Exchange (IKE) protocol
- UDP port 4500 for IKE NAT-Traversal
- Protocol 50 for Encapsulated Security Payload (ESP) IPsec packets
- Protocol 51 for Authenticated Header (AH) IPsec packets (uncommon)
- In case that the node will expose a subnet to the other side IP Forwarding needs to be enabled. This can be done through the WebUI or through the cli as normal user with admin Rights.
- IP forwarding through WebUI
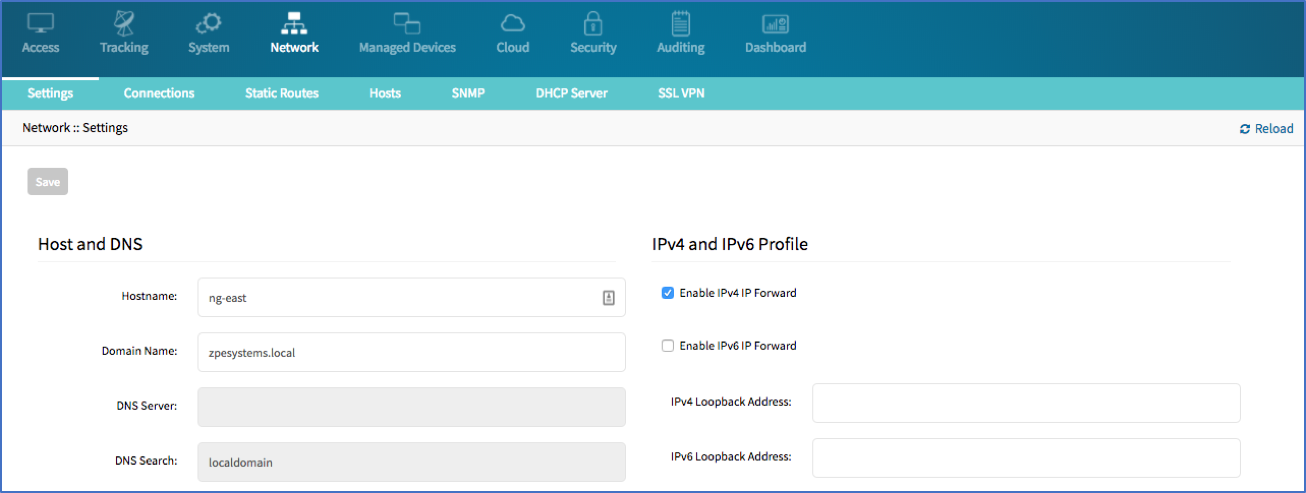
- Login with an admin user and navigate to Network::Settings
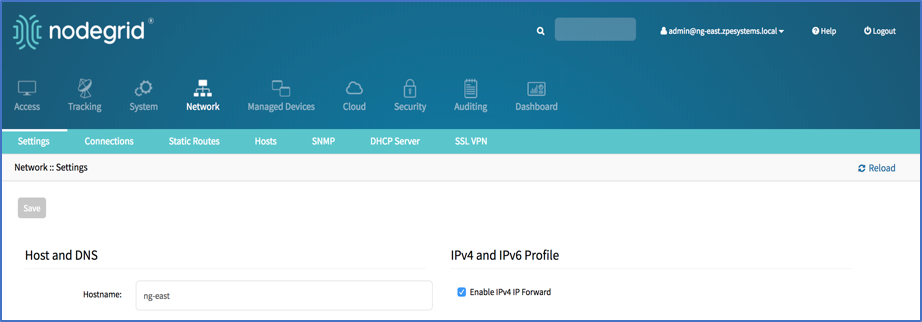
- Enable IPv4 or IPv6 Forward as required, by ticking the box
- Save Settings
- IP Forwarding Through CLI
- Navigate to network settings
- Enable IP forwarding for IPv4 or IPv6
- Commit the change
- Prepare basic kernel networking attributes
- As root user on the shell edit file /etc/sysctl.conf to set reverse path filtering for Ethernet interfaces which will be used for the IPSec tunnel. Set the value either to 0 = disabled or 2 = not strict. By adding the following line to the end of the file.
- Activate the changes
root@ng-east:~#ipsec initnss
Nodegrid requires the firewall rules to allow IPSec traffic
[admin@ng-east /]# cd /settings/network_settings/
[admin@ng-east network_settings]# set enable_ipv4_ip_forward=yes
[+admin@ng-east network_settings]# commit
Format:
net.ipv4.conf..rp_filter=0
Example:
net.ipv4.conf.eth1.rp_filter=0
root@ng-west:~# sysctl -p net.ipv4.conf.default.rp_filter = 1 net.ipv4.conf.all.rp_filter = 1 net.ipv4.conf.eth1.rp_filter = 1 vm.max_map_count = 262144 kernel.pty.max = 8192 kernel.core_uses_pid = 1 kernel.kptr_restrict = 2 kernel.sysrq = 0 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.default.accept_redirects = 0 net.ipv6.conf.all.accept_redirects = 0 net.ipv6.conf.default.accept_redirects = 0 net.ipv4.tcp_challenge_ack_limit = 99999999 net.ipv4.tcp_timestamps = 0 net.ipv6.conf.default.optimistic_dad = 1 net.ipv6.conf.all.optimistic_dad = 1 net.ipv4.conf.all.send_redirects = 0 net.ipv4.conf.default.accept_source_route = 0 net.ipv4.ip_forward = 1 net.ipv6.conf.all.forwarding = 0
Configuration of IPSec
This section outlines the general configuration steps which can be used to configure the desired connection.
- Prepare the Nodegrid. (See this document)
- Ensure the that one of authentication methods is prepared
- Create an IPSec configuration file and as need a secrets file
- Distribute and exchange configuration files and Keys as required to all nodes
- Test the connection
Configuration Examples
Host to Host
- How to Configure IPSec Host to Host tunnel with Pre-Shared Key
- How to Configure IPSec Host to Host tunnel with RSA Keys
- How to Configure IPSec Host to Host tunnel with Certificates
Host to Site
- How to Configure IPSec Host to Site tunnel with Pre-Shared Key
- How to Configure IPSec Host to Site tunnel with RSA Keys
- How to Configure IPSec Host to Site Tunnel with Certificate
Site to Site
- How to Configure IPSec Site to Site tunnel with Pre-Shared Key
- How to Configure IPSec Site to Site tunnel with RSA Keys
- How to Configure IPSec Site to Site tunnel with Certificate
Related Articles
How to configure IPSec Host to Site tunnel with Pre-Shared Key
Version 0.1 (02 May 2018) Overview Host to Site configurations are very similar to Host to Host configurations, especially the authentication methods are the same. Added changes to the configurations are the values for rightsourceip and rightsubnets. ...How to create Pre-shared Keys for IPSec
Version 0.1 (02 May 2018) Prepare Pre-shared Keys In case Pre-shared Key will be used to authenticate IPSec tunnels, they need to be created on a Nodegrid system before they can be used. To create a Pre-Shared key on a Nodegrid use the below steps. ...How to Configure IPSec Host to Host Tunnel with Pre-Shared Key
Version 0.1 (02 May 2018) Overview Host to Host configurations allow two nodes to establish a tunnel between them. The encrypted communication will be limited just to the two nodes involved. Figure 11: Host to Host Configuration Example Details Host ...How to Configure IPSec Site to Site Tunnel with Pre-Shared Key
Version 0.1 (02 May 2018) Overview Site to Site Configurations are further extension to host to site configurations. Communication is in this case expanded between multiple subnet on both sites of the connection. Subnet and communication IP addresses ...How to Configure IPSec Host to Site tunnel with RSA Keys
Version 0.1 (02 May 2018) Overview Host to Site configurations are very similar to Host to Host configurations, especially the authentication methods are the same. Added changes to the configurations are the values for rightsourceip and ...