IPSec VPN support
Virtual Private Network (VPN) Overview
A Virtual Private Network (VPN) is used to provide a secure means of communication among remote computers across networks, such as the Internet or a public WAN in general. VPN creates an encrypted connection, known as VPN tunnel, and all data traffic and communication are passed through this secure tunnel, keeping user data secure and private. To accomplish this, several types of VPN security protocols can be used.
The Nodegrid solution supports IPSec as well as SSL VPN.
In this How to we will focus on how the Nodegrid solution can utilise the Internet Protocol Security (IPSec) to establish a VPN tunnel between participants (“endpoints”).
There are many different configuration options available and the how to will focus on some of the most common configurations.
IMPORTANT: As the Nodegrid node will be directly be exposed to the Internet. Is it strongly recommended to secure the appliance. Built-in features can be used for this like:
- Configuring Firewall
- Enabling Fail-2-Band
- Changing all default passwords with strong passwords
- Disabling services which are not required
It is beyond the scope of this guide to cover these aspects in detail.
Authentication Methods
Multiple Authentication methods are available together with IPSec and the Nodegrid solution. Some of these are very easy to implement, like Pre-Shared keys and RSA keys but offer limited flexibility in larger setups while certificates required more initial configuration and setup but offer the flexibility and consistency to easily manage and maintain larger setups.
Pre-shared Keys
Pre-shared Keys is a simple and the least secure method to secure an IPSec connection. Pre-shared keys are a combination of characters which represent a secret. Both nodes need to share the same secret. Nodegrid supports pre-shared keys with a minimum length of 32 characters. The maximum length is much higher but due to compatibility reasons with other vendors we will use a length of 64 bit for the examples below. In general, the longer the pre-shared is the more secure it is.
RSA Keys
RSA Keys or Raw RSA keys are commonly used for static configurations between single or a small number of hosts. The nodes manually configured to have each other’s RSA keys as part of the configuration.
X.509 Certificates
X.509 Certificate authentications are typically used for larger deployments with a small to large number of nodes. The RSA keys of the individual nodes are signed by a central Certificate Authority (CA). The Certificate Authority is used to maintain the trust relationship between the nodes including revocation of trust for specific nodes. The Nodegrid solutions support for this purpose public and private CA’s. Further to this can the Nodegrid Solution be used to host and manage its own Certificate Authority for the purpose of the IPSec communication.
Connection Scenarios
IPSec supports many different connection scenarios, starting from communication just between 2 nodes to communication of one node to multiple nodes, communication limited just to the nodes involved or expanding beyond the directly involved nodes to the networks access able behind the nodes.
Due to the multitude of communication options, examples are provided for some of the most common scenarios.
Host to Host
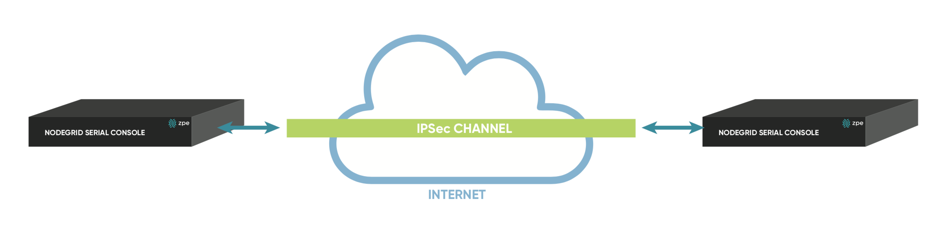
Figure 1: Host to Host: Direct Connection
Host to Host communication means that 2 nodes have a VPN tunnel open which connects them directly. The communication which is exchanged through the tunnel is limited to direct communication between them. None of the packages will be routed or forwarded. This is essentially a point to point communication between 2 nodes.
Host to Site
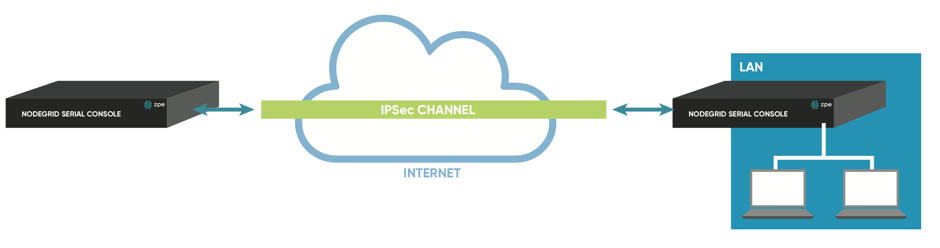
Figure 3: Host to Site: Direct Connection
In a Host to Site communication scenario one node establishes a VPN tunnel to a 2nd node. Communication is limited on one site to the specific node and on the other side to all devices in a range of subnet which are accessible by the 2nd node
Site to Site
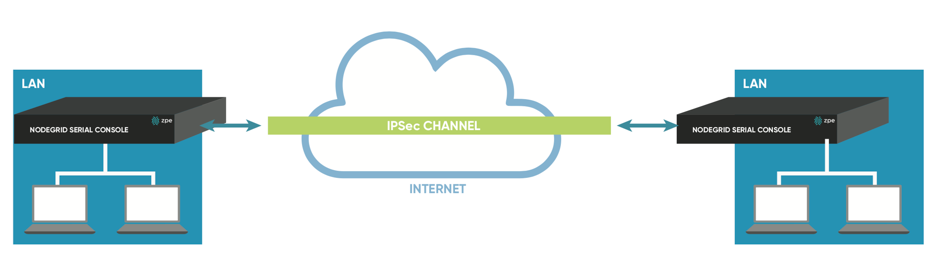
Figure 5:Site to Site: Direct Connection
In a Site to Site communication the tunnel is as before established between 2 nodes, communication is allowed to specific subnet on both sides, allowing for communication between devices on either side of the connection.
Host to Multi Site
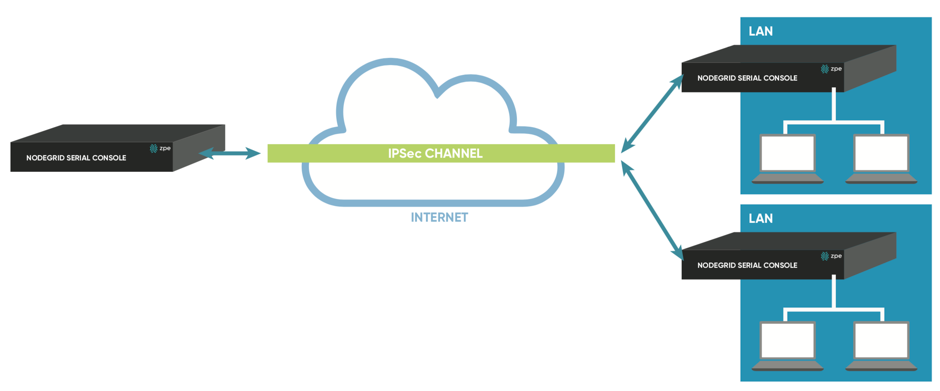
Figure 7: Host to Multi Site: Direct Connection
Multi-Site communication scenarios can be created by either creating individual VPN connections between hosts or by specific multi-site configurations.
The later greatly improve scalability and manageability of the connection setup
As the name indicates allows a Host to multi-site communication multiple nodes to connect to the same node. Typical scenario for this would be that remote offices have a VPN connection to the main office. In this specific scenario would the communication be limited to the one node and devices on specified subnets in the remote locations.
Site to Multi Site
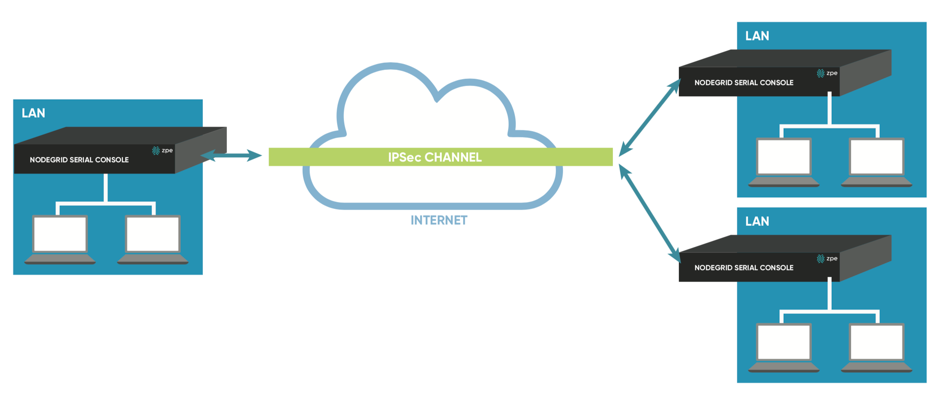
Figure 9: Site to Multi Site: Direct Connection
This scenario is probably the most common form for enterprise VPN setups. It is similar to the Host to multi-side option but communication is allowed to specific subnet on either side, where by the West node would have access to all specified subnet on any of the sites but the remote sites have only access to subnet exposed by the West node.
| | Host to Host | Host to Site | Site to Site | Host to Multi-Site | Site to Multi-Site |
|---|---|---|---|---|---|
| Pre-shared Keys | possible | possible | possible | possible | possible |
| RSA Key | Recommended | Recommended | Recommended | possible | possible |
| X.509 Certificates | Recommended | Recommended | Recommended | Recommended | Recommended |
Related Articles
How to create Pre-shared Keys for IPSec
Version 0.1 (02 May 2018) Prepare Pre-shared Keys In case Pre-shared Key will be used to authenticate IPSec tunnels, they need to be created on a Nodegrid system before they can be used. To create a Pre-Shared key on a Nodegrid use the below steps. ...How to Configure IPSec Host to Host Tunnel with Pre-Shared Key
Version 0.1 (02 May 2018) Overview Host to Host configurations allow two nodes to establish a tunnel between them. The encrypted communication will be limited just to the two nodes involved. Figure 11: Host to Host Configuration Example Details Host ...How to configure IPSec Host to Site tunnel with Pre-Shared Key
Version 0.1 (02 May 2018) Overview Host to Site configurations are very similar to Host to Host configurations, especially the authentication methods are the same. Added changes to the configurations are the values for rightsourceip and rightsubnets. ...How to Configure IPSec Site to Site Tunnel with Pre-Shared Key
Version 0.1 (02 May 2018) Overview Site to Site Configurations are further extension to host to site configurations. Communication is in this case expanded between multiple subnet on both sites of the connection. Subnet and communication IP addresses ...How to Prepare a Nodegrid Node for IPSec
Version 0.1 (02 May 2018) Overview Nodegrid comes with all the required tools to run and configure IPSec pre-installed, but IPSec is by default not configured and a few preparation steps on every node need to be performed before the first VPN ...