How to Configure Firewall on a Nodegrid
Overview
The Nodegrid platform comes with its own firewall which is based on iptables. The WebUI and the CLI provide an easy way of creating and managing the firewall.
By default, the firewall accepts all incoming traffic. Specifically, if the Nodegrid is exposed to an internet connection either directly or indirectly is it recommended to secure the Nodegrid with a valid firewall configuration. This guide will provide a starting point for this.
How to Configure a new Firewall rule
All defined rules will persist through a reboot.
In case that a rule prevents access to the node, the rules can be adjusted through the local console port of the node.
Note: the following rules must always be applied to a Nodegrid as they are required for a normal operation
| Service | Source | Destination | Direction | Protocol | Port | Comments |
|---|---|---|---|---|---|---|
| loopback | INBOUND | IPv4 | ||||
| loopback | OUTBOUND | IPv4 | ||||
| loopback | INBOUND | IPv6 | ||||
| loopback | OUTBOUND | IPv6 |
A list of commonly used Firewall Rules on a Nodegrid can be found in Firewall Rules for the Nodegrid platform.
Create a new Rule
Create a new Rule through CLI
- login with an admin account
- navigate to the desired firewall chain. By default, the following 6 Chains are available
- IPv4 INPUT
- IPv4 INPUT
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/INPUT/
- IPv4 FORWARD
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/FORWARD/
- IPv4 OUTPUT
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/OUTPUT/
- IPv6 INPUT
[admin@nodegrid /]# cd /settings/ipv6_firewall/chains/INPUT/
- IPv6 FORWARD
[admin@nodegrid /]# cd /settings/ipv6_firewall/chains/FORWARD/
- IPv6 OUTPUT
[admin@nodegrid /]# cd /settings/ipv6_firewall/chains/OUTPUT/
- Type add to create a new rule
[admin@nodegrid INPUT]# add
- Use the set command to create the new rule settings. Press TAB twice to see all available options
[admin@nodegrid {INPUT}]# set target=ACCEPT source_net4=192.168.1.1
- Use the save command to create and activate the new rule
[admin@nodegrid {INPUT}]# save
- use the show command to see the current values for the rule
[admin@nodegrid 2]# show target = ACCEPT source_net4 = 192.168.1.1 destination_net4 = protocol = tcp source_port = destination_port = 443 tcp_flag_syn = any tcp_flag_ack = any tcp_flag_fin = any tcp_flag_rst = any tcp_flag_urg = any tcp_flag_psh = any input_interface = any output_interface = any fragments = all_packets_and_fragments reverse_match_for_source_ip|mask = no reverse_match_for_destination_ip|mask = no reverse_match_for_source_port = no reverse_match_for_destination_port = no reverse_match_for_protocol = no reverse_match_for_tcp_flags = no reverse_match_for_icmp_type = no reverse_match_for_input_interface = no reverse_match_for_output_interface = no reject_with = port_unreacheable log_level = debug log_prefix = log_tcp_sequence_numbers = no log_options_from_the_tcp_packet_header = no log_options_from_the_ip_packet_header = no
- A list of currently active IPv4 rules can be see with the command shell sudo /usr/sbin/iptables -L -nvx
[admin@nodegrid /]# shell sudo /usr/sbin/iptables -L -nvx Chain INPUT (policy ACCEPT 110 packets, 13509 bytes) pkts bytes target prot opt in out source destination 1182 132492 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0 0 0 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 1182 132492 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0 59 32478 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0
- A list of currently active IPv6 rules can be see with the command shell sudo /usr/sbin/ip6tables -L -nvx
[admin@nodegrid /]# shell sudo /usr/sbin/ip6tables -L -nvx Chain INPUT (policy DROP 1 packets, 72 bytes) pkts bytes target prot opt in out source destination 2 132 ACCEPT all lo * ::/0 ::/0 0 0 ACCEPT all * * ::1 ::/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 8384 packets, 428444 bytes) pkts bytes target prot opt in out source destination 2 132 ACCEPT all * * ::1 ::/0
Create a new Rule through WebUI
- Login with an admin account
- Go to Security::Firewall
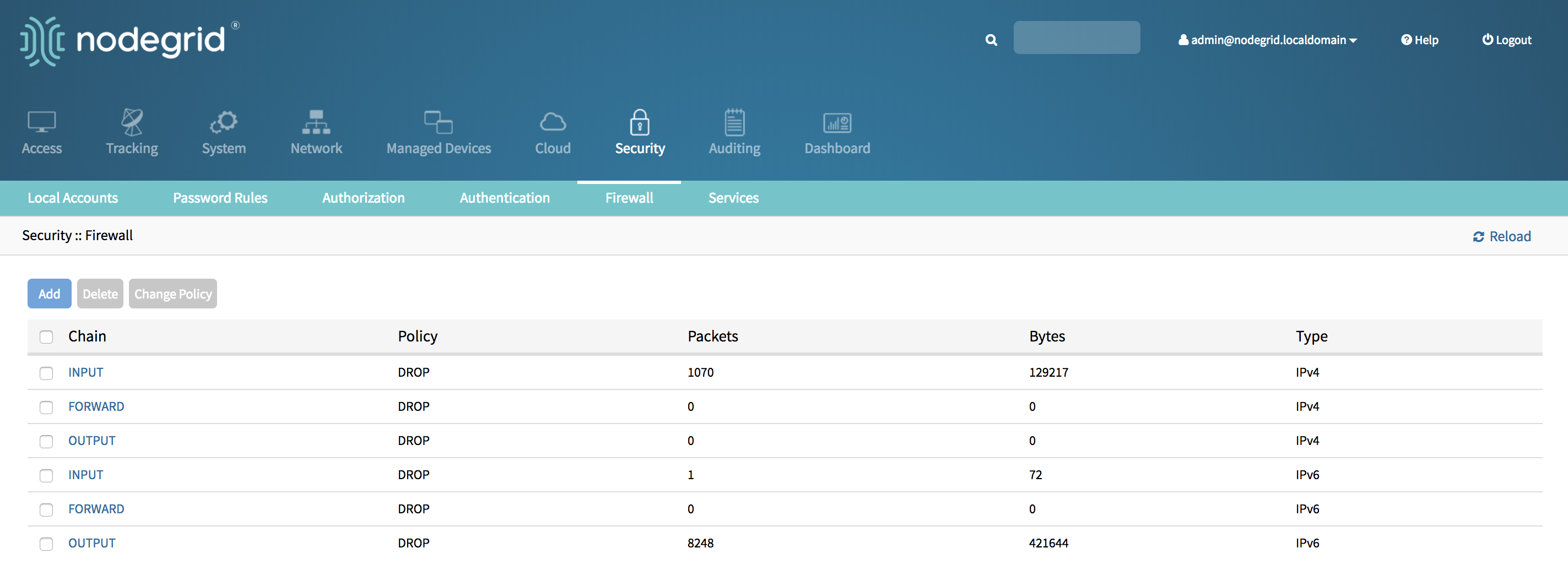
- Click on the desired Chain, by default the following 6 chains are available
- INPUT - Type IPv4
- FORWARD - Type IPv4
- OUTPUT - Type IPv4
- INPUT - Type IPv6
- FORWARD - Type IPv6
- OUTPUT - Type IPv6
- Click on add to create a new rule
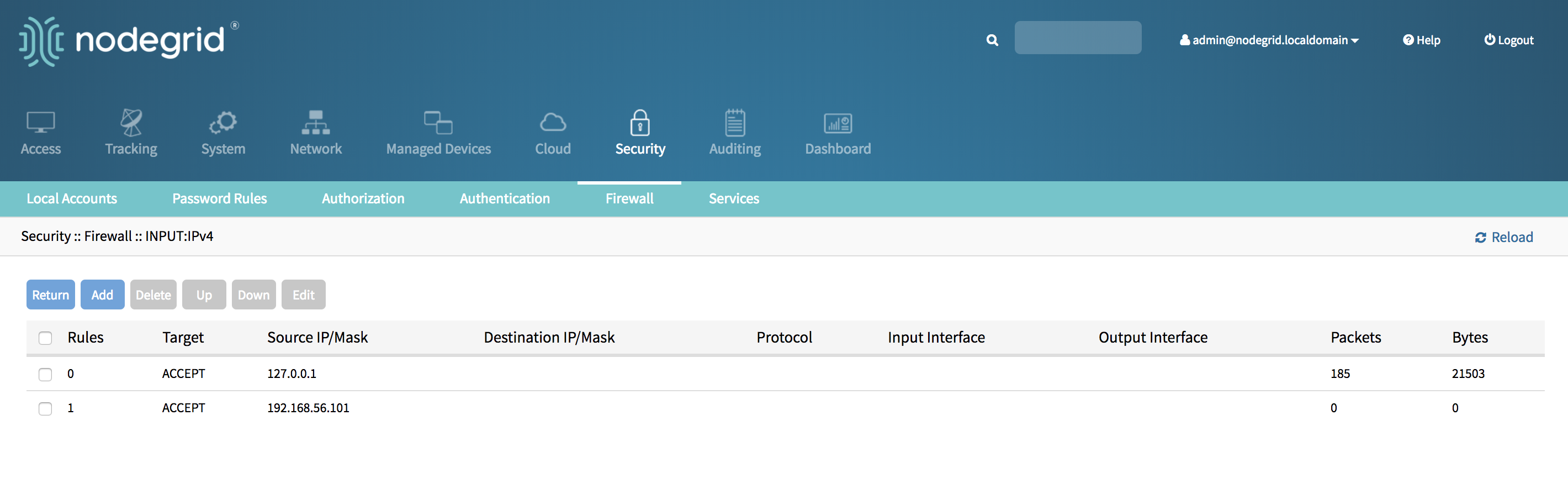
- Enter the desired values for the new rule and click on save.
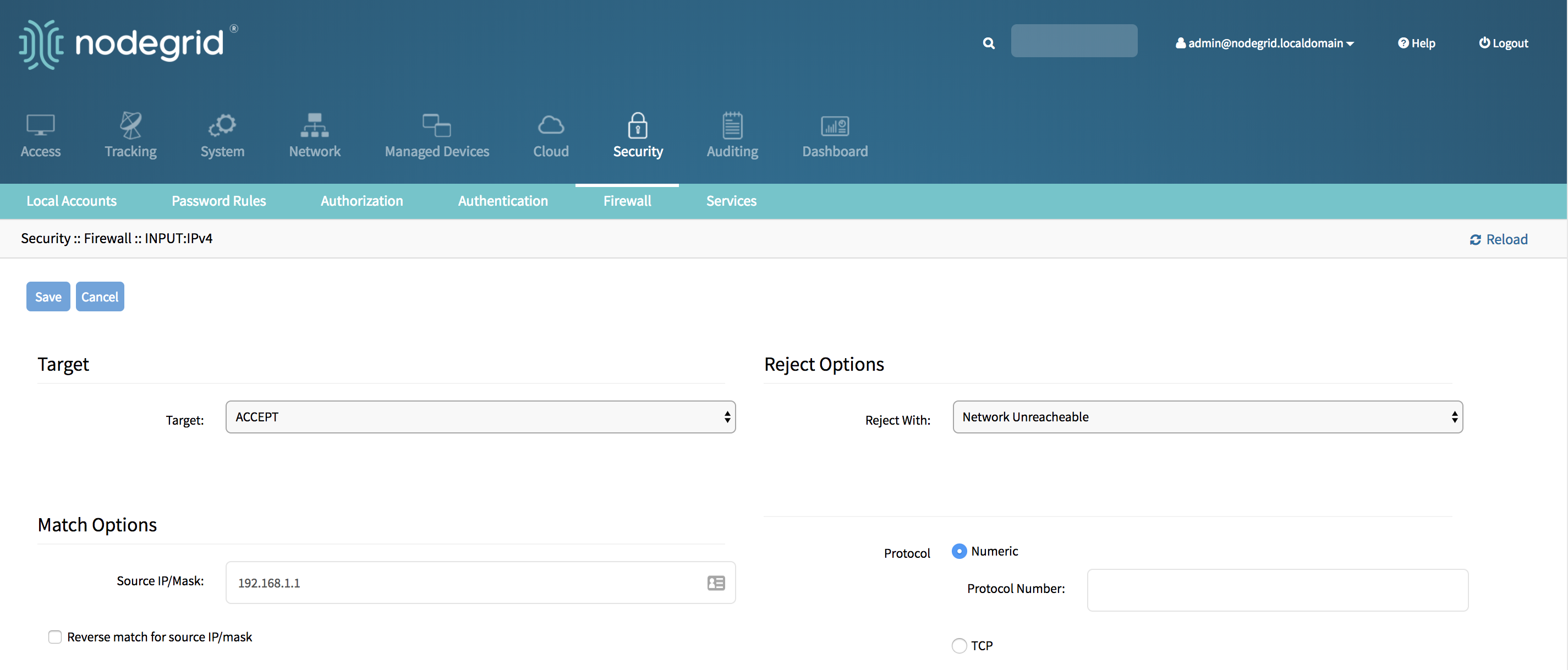
- The new rule will saved and will be effective immediately
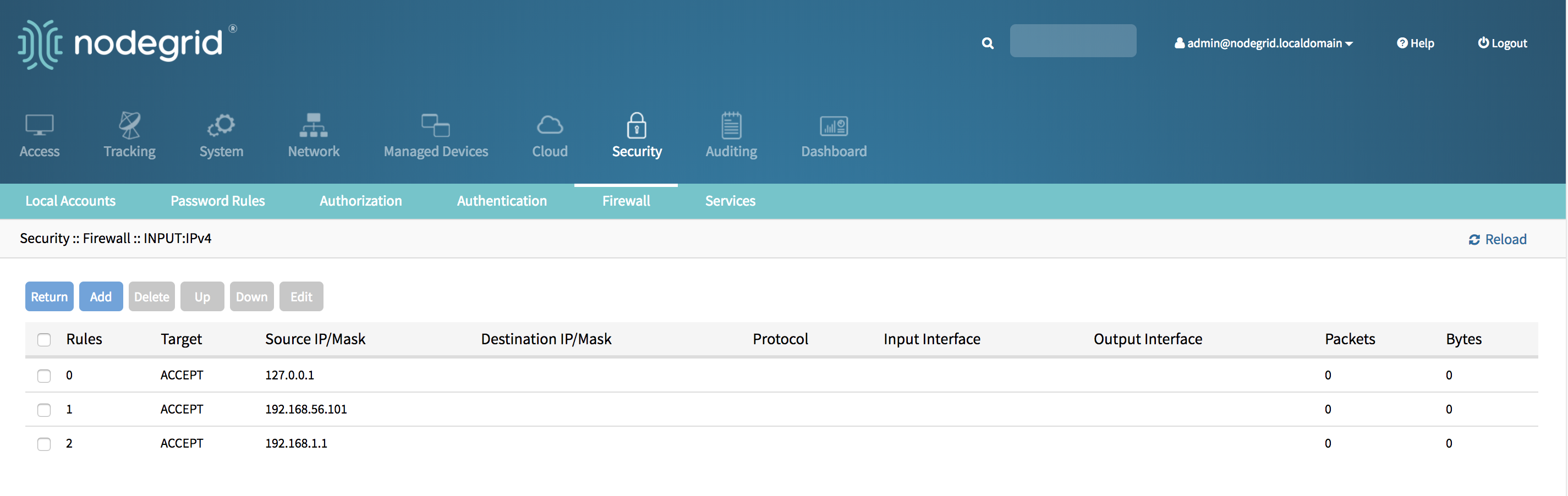
Delete a Rule
Delete a Rule through CLI
- Login with an admin account
- Navigate to the firewall Chain which contains the rule
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/INPUT/
- List all available rules with the show command
[admin@nodegrid INPUT]# show rules target source net4 destination net4 protocol input interface output interface packets bytes ===== ====== ============== ================ ======== =============== ================ ======= ======= 0 ACCEPT 127.0.0.1 0 0 1 ACCEPT 192.168.56.101 0 0 2 ACCEPT 192.168.1.1 tcp 104007 5150785
- Type delete together with the rule number to delete a rule and to activate the change
[admin@nodegrid INPUT]# delete 2
- A list of currently active IPv4 rules can be see with the command shell sudo /usr/sbin/iptables -L -nvx
[admin@nodegrid /]# shell sudo /usr/sbin/iptables -L -nvx Chain INPUT (policy ACCEPT 110 packets, 13509 bytes) pkts bytes target prot opt in out source destination 1182 132492 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0 0 0 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 1182 132492 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0 59 32478 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0
- A list of currently active IPv6 rules can be see with the command shell sudo /usr/sbin/ip6tables -L -nvx
[admin@nodegrid /]# shell sudo /usr/sbin/ip6tables -L -nvx Chain INPUT (policy DROP 1 packets, 72 bytes) pkts bytes target prot opt in out source destination 2 132 ACCEPT all lo * ::/0 ::/0 0 0 ACCEPT all * * ::1 ::/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 8384 packets, 428444 bytes) pkts bytes target prot opt in out source destination 2 132 ACCEPT all * * ::1 ::/0
Delete a Rule through WebUI
- Login with an admin account
- Go to Security::Firewall

- Click on the Chain which contains the rule to see a list of current rules
- Tick the rule to be deleted
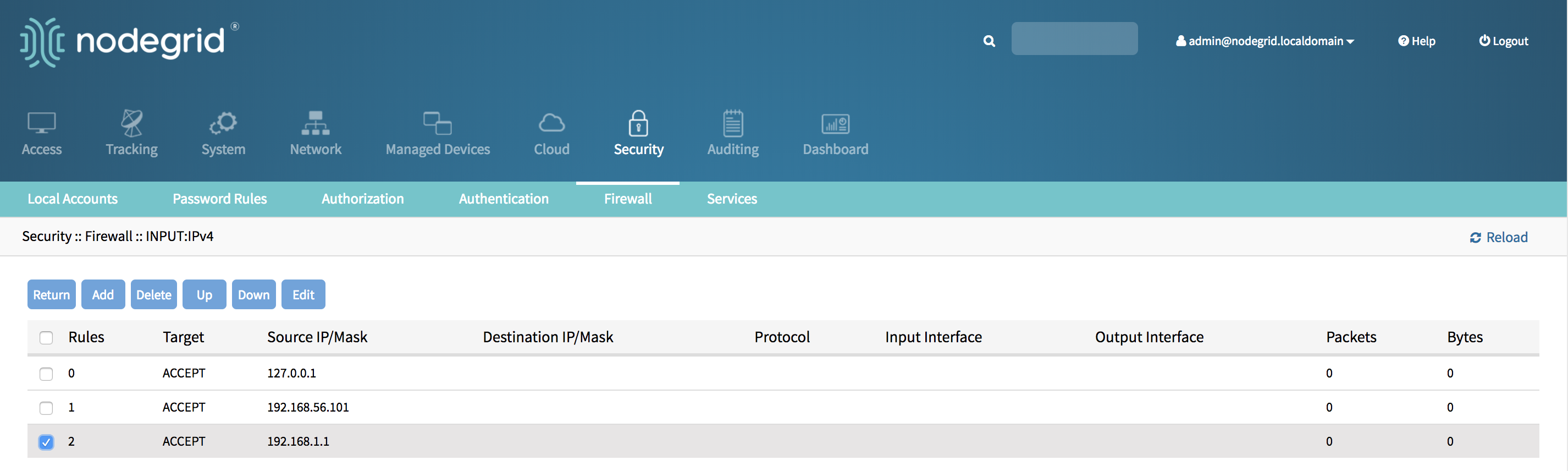
- Click on Delete
- The rule will deleted and the change will be effective immediately

Edit an existing Rule
Edit an existing Rule through CLI
- login with an admin account
- navigate to the firewall Chain which contains the rule
- list all available rules with the show command
[admin@nodegrid INPUT]# show rules target source net4 destination net4 protocol input interface output interface packets bytes ===== ====== ============== ================ ======== =============== ================ ======= ====== 0 ACCEPT 127.0.0.1 3979 251243 1 ACCEPT 192.168.56.101 0 0 2 ACCEPT 192.168.1.1 0 0
- Navigate into the rule to be change with it’s rule number
[admin@nodegrid INPUT]# cd 2/
- Use the set command to create the new rule settings. Press TAB twice to see all available options
[admin@nodegrid 2]# set protocol=tcp destination_port=443
- Use the commit command to save and activate the changes
[+admin@nodegrid 2]# commit
- use the show command to see the current values for the rule
[admin@nodegrid 2]# show target = ACCEPT source_net4 = 192.168.1.1 destination_net4 = protocol = tcp source_port = destination_port = 443 tcp_flag_syn = any tcp_flag_ack = any tcp_flag_fin = any tcp_flag_rst = any tcp_flag_urg = any tcp_flag_psh = any input_interface = any output_interface = any fragments = all_packets_and_fragments reverse_match_for_source_ip|mask = no reverse_match_for_destination_ip|mask = no reverse_match_for_source_port = no reverse_match_for_destination_port = no reverse_match_for_protocol = no reverse_match_for_tcp_flags = no reverse_match_for_icmp_type = no reverse_match_for_input_interface = no reverse_match_for_output_interface = no reject_with = port_unreacheable log_level = debug log_prefix = log_tcp_sequence_numbers = no log_options_from_the_tcp_packet_header = no log_options_from_the_ip_packet_header = no
- A list of currently active IPv4 rules can be see with the command shell sudo /usr/sbin/iptables -L -nvx
[admin@nodegrid 2]# shell sudo /usr/sbin/iptables -L -nvx Chain INPUT (policy ACCEPT 38 packets, 2372 bytes) pkts bytes target prot opt in out source destination 385 38206 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0 0 0 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0 0 0 ACCEPT tcp -- * * 192.168.1.1 0.0.0.0/0 tcp dpt:443 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 385 38206 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0 24 2828 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0
- A list of currently active IPv6 rules can be see with the command shell
sudo /usr/sbin/ip6tables -L -nvx
[admin@nodegrid 2]# shell sudo /usr/sbin/ip6tables -L -nvx Chain INPUT (policy DROP 1 packets, 72 bytes) pkts bytes target prot opt in out source destination 2 132 ACCEPT all lo * ::/0 ::/0 0 0 ACCEPT all * * ::1 ::/0 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 8822 packets, 451048 bytes) pkts bytes target prot opt in out source destination 2 132 ACCEPT all * * ::1 ::/0
Edit an existing Rule through WebUI
- Login with an admin account
- Go to Security::Firewall

- Click on the Chain which contains the rule to see a list of current rules
- Tick the rule to be changed

- Click on Edit
- Adjusted the setting as required and click on Save
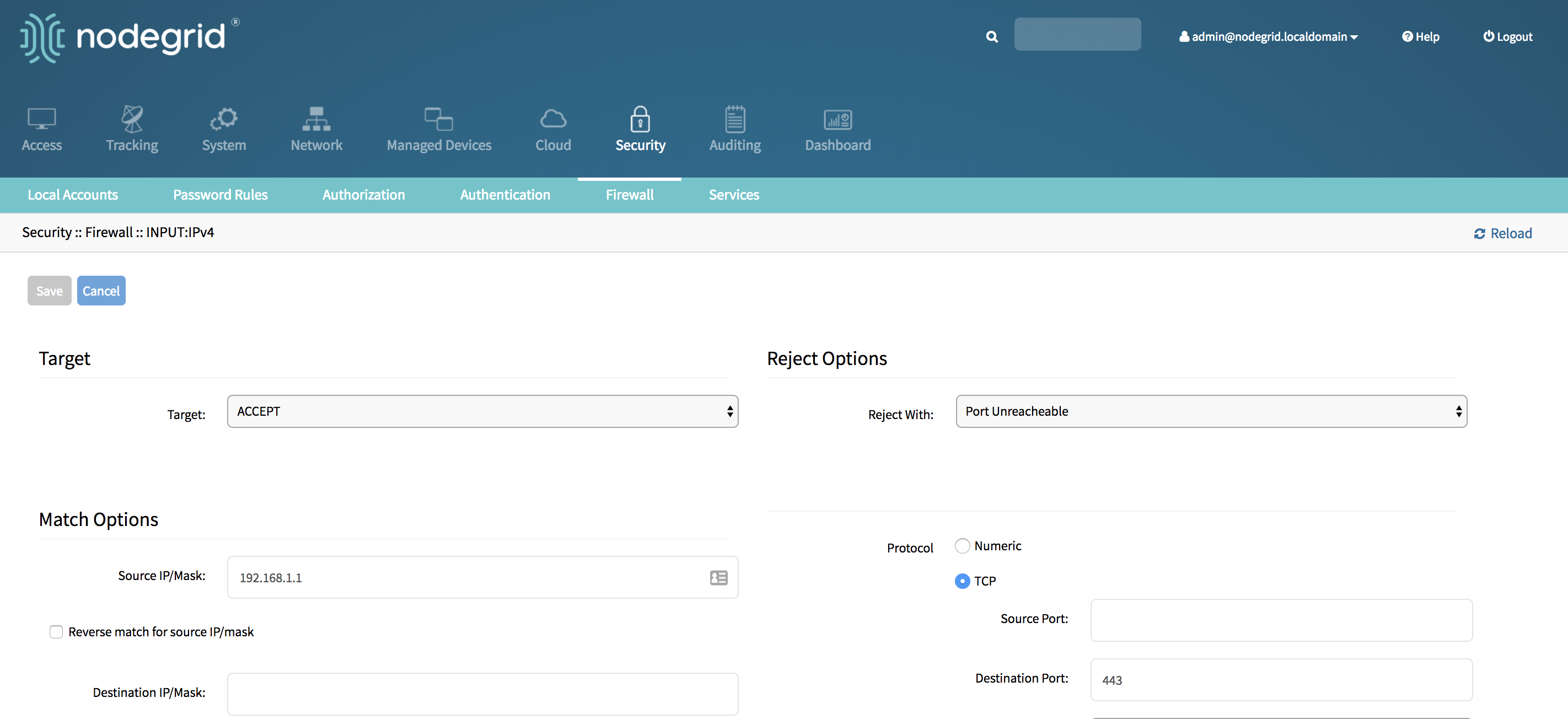
- The new rule will saved and will be effective immediately
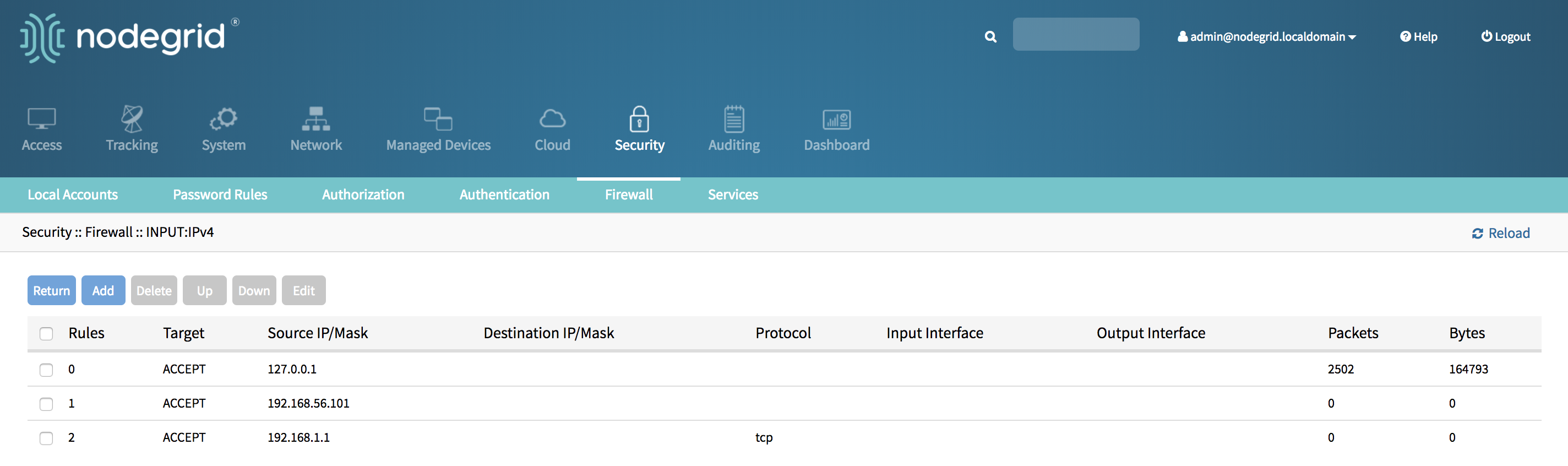
Set Default Policy for a Chain
Set default Policy for a Chain through CLI
Before changing the default policy for a chain to drop ensure that all required accept rules have been entered. After the change takes effect all not allowed access will be dropped.
- login with an admin account
- navigate to the firewall policy to changed
- IPv4 Policies are located
- IPv4 Policies are located
[admin@nodegrid /]# cd /settings/ipv4_firewall/policy/
- IPv6 Policies are located
[admin@nodegrid /]# cd /settings/ipv6_firewall/policy/
- Use the show command to list the current settings
[admin@nodegrid policy]# show input = accept output = accept forward = accept
- Change the default policy for a chain with the set command
[admin@nodegrid policy]# set input=drop
- Use the commit command to save and activate the changes
[+admin@nodegrid policy]#commit
Set default Policy for a Chain through WebUI
Before changing the default policy for a chain to drop ensure that all required accept rules have been entered. After the change takes effect all not allowed access will be dropped.
- Login with an admin account
- Go to Security::Firewall

- Tick the Chain for which the default policy should be changed
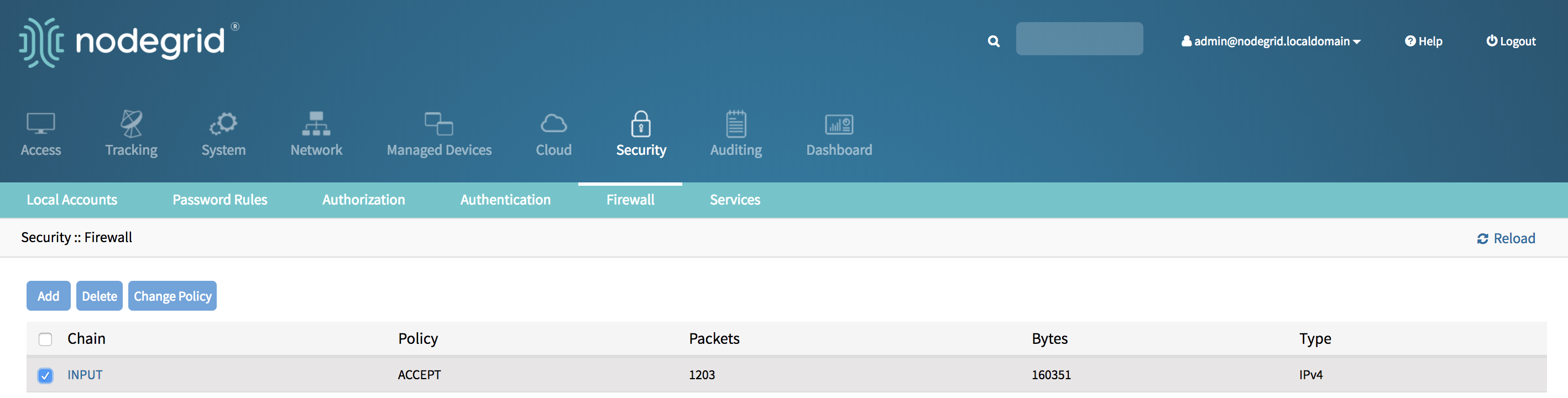
- Click on Change Policy
- Set the new default policy and accept the change with Save.
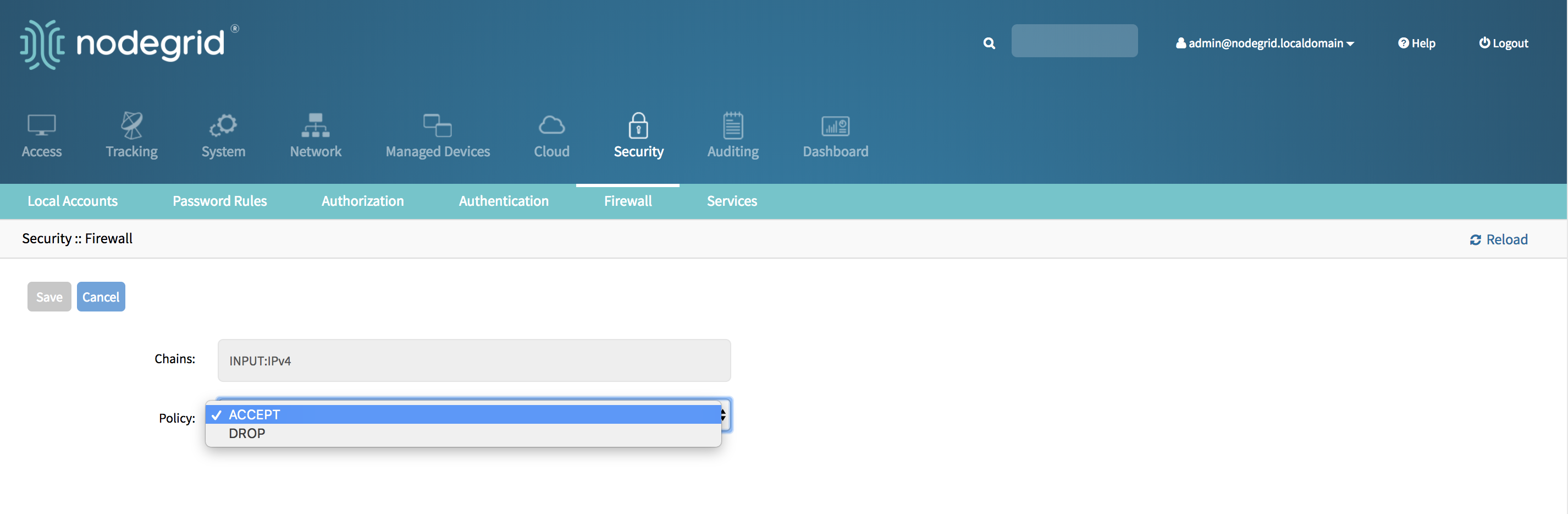
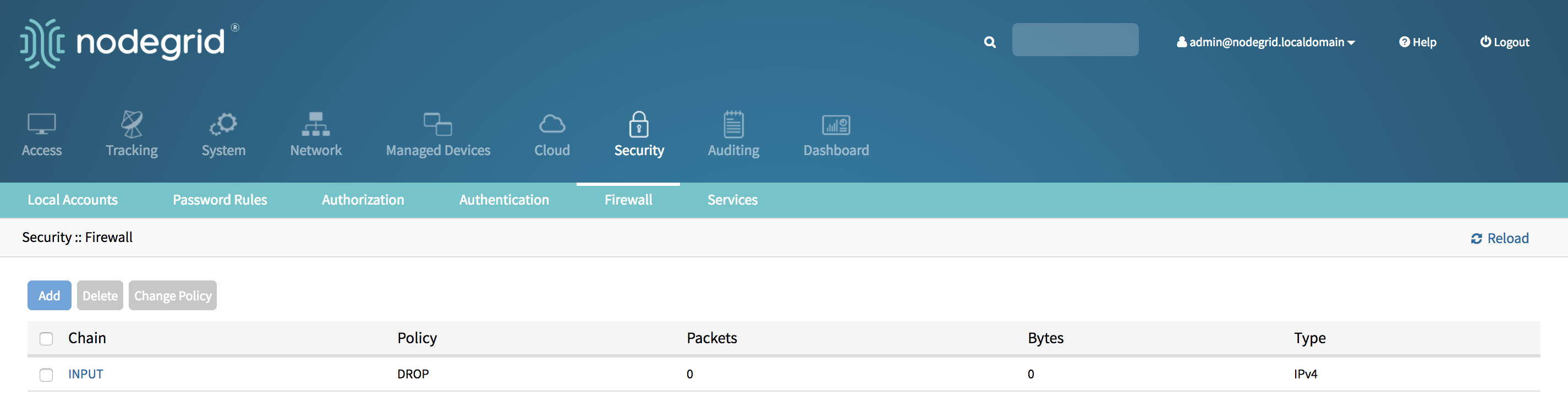
- The new Policy will saved and will be effective immediately
Related Articles
Firewall Rules for the Nodegrid Platform
Version 0.2 (17 May 2018) Overview This guide lists all required and recommended firewall rules, to ensure a proper working of the solution. The list will need to be adjusted based on specific customer requirements. By default will the firewall will ...Creating a New Firewall rule to block an Ip address or a network
There are six default chains to configure firewall rules. Three for IPv4 and three for IPv6. These chains are input , output and forward packets. One can make additional user chain if required. For each chain, policy can be created. Configuration ...Use any interface for Iptables from Nodegrid UI
New for Nodegrid 6.0 and later, you can now use any interface in Iptables firewall or NAT rules. You can use interfaces that don't show in the interface drop-down menu. You can also use an interface that doesn't exist yet, such as VTI interfaces for ...Setting a firewall rule to block a single IP address
Nodegrid can act as a firewall to filter traffic. It has six build in chains ( three for ipv4 and three for ipv6 ) - INPUT, OUTPUT and FORWARD Default policy can be assigned for each chain. For each chain, rules can be added deleted and modified. ...Company's Firewall configuration: what resources need to be opened in Firewall for the Nodegrid appliances to connect to ZPE Cloud?
ZPE Cloud uses some IP addresses and hostnames that may be blocked by the Firewall rules. This can prevent the Nodegrid appliances from connecting to the Cloud and/or utilizing specific ZPE Cloud features. ZPE Cloud utilizes TCP port 443 for ...